Ransomware and Silence Locker control panel
(Publication) Google search: [1]
| Ransomware and Silence Locker control panel | |
|---|---|
| |
| Botnet | Silence Locker |
| Malware | |
| Botnet/malware group | |
| Exploit kits | |
| Services | |
| Feature | |
| Distribution vector | |
| Target | |
| Origin | |
| Campaign | |
| Operation/Working group | |
| Vulnerability | |
| CCProtocol | |
| Date | 2012 / |
| Editor/Conference | Symantec |
| Link | http://www.symantec.com/connect/blogs/ransomware-and-silence-locker-control-panel (Archive copy) |
| Author | Peter Coogan |
| Type | |
Abstract
“ Ransomware is a threat that continues to grow in popularity with cybercriminals due to its success rate and monetary potential. In past blogs such as Rampant Ransomware we have discussed some different Ransomware variants and techniques. Now we have encountered yet another new variant identified as Trojan.Ransomlock.K.
While finding a new Ransomware variant is no real surprise, during analysis we found an active command-and-control (C&C) server login used by the threat.
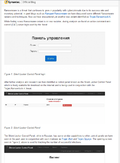
Figure 1. Silent Locker Control Panel login
After further analysis and research we then identified a control panel known as the Silent Locker Control Panel which is freely available for download on the Internet and is being used in conjunction with the Trojan.Ransomlock.K threat.
Bibtex
@misc{Lua error: Cannot create process: proc_open(/dev/null): failed to open stream: Operation not permitted2012BFR993,
editor = {Symantec},
author = {Peter Coogan},
title = {Ransomware and Silence Locker control panel},
date = {16},
month = Jun,
year = {2012},
howpublished = {\url{http://www.symantec.com/connect/blogs/ransomware-and-silence-locker-control-panel}},
}