Kelihos/Hlux botnet returns with new techniques
Jump to navigation
Jump to search
(Publication) Google search: [1]
| Kelihos/Hlux botnet returns with new techniques | |
|---|---|
| |
| Botnet | Kelihos, Hlux |
| Malware | |
| Botnet/malware group | |
| Exploit kits | |
| Services | |
| Feature | |
| Distribution vector | |
| Target | |
| Origin | |
| Campaign | |
| Operation/Working group | |
| Vulnerability | |
| CCProtocol | |
| Date | 2012 / 31 janvier 2011 |
| Editor/Conference | Kaspersky lab |
| Link | http://www.securelist.com/en/blog/655/Kelihos Hlux botnet returns with new techniques (Archive copy) |
| Author | Maria Garnaeva |
| Type | |
Abstract
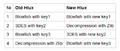
“ t has been four months since Microsoft and Kaspersky Lab announced the disruption of Kelihos/Hlux botnet. The sinkholing method that was used has its advantages — it is possible to disable a botnet rather quickly without taking control over the infrastructure.However,as this particular case showed, it is not very effective if the botnet’s masters are still at large.
Not long after we disrupted Kehilos/Hlux, we came across new samples that seemed to be very similar to the initial version. After some investigation, we gathered all the differences between the two versions. This is a summary of our findings: ...
Bibtex
@misc{Lua error: Cannot create process: proc_open(/dev/null): failed to open stream: Operation not permitted2012BFR842,
editor = {Kaspersky lab},
author = {Maria Garnaeva},
title = {Kelihos/Hlux botnet returns with new techniques},
date = {Error: Invalid time.},
month = Error: Invalid time.,
year = {2012},
howpublished = {\url{http://www.securelist.com/en/blog/655/Kelihos_Hlux_botnet_returns_with_new_techniques}},
}