Anaru malware now live and ready to steal
Jump to navigation
Jump to search
(Publication) Google search: [1]
| Anaru malware now live and ready to steal | |
|---|---|
| |
| Botnet | Anaru |
| Malware | |
| Botnet/malware group | |
| Exploit kits | |
| Services | |
| Feature | |
| Distribution vector | |
| Target | |
| Origin | |
| Campaign | |
| Operation/Working group | |
| Vulnerability | |
| CCProtocol | |
| Date | 2012 / 07 septembre 2012 |
| Editor/Conference | Symantec |
| Link | http://www.symantec.com/connect/ko/blogs/anaru-malware-now-live-and-ready-steal (Archive copy) |
| Author | Joji Hamada |
| Type | |
Abstract
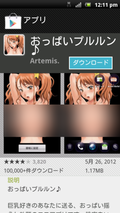
“ Recently, I blogged about a famous Anime character named Anaru who was being used to steal contact details from Android devices. At the time of investigation, the app appeared to be in a testing phase, with the possibility that it might have been created for fun. However, the app’s creators now appear to have moved to the next level and are now actively enticing Android device owners to install the app.
The Anaru malware, which Symantec detects as Android.Maistealer, is now hosted on multiple, dedicated websites that resemble Google Play. The app is not available on Google Play, as far as I am aware of, and is only available on these dedicated websites.
Bibtex
@misc{Lua error: Cannot create process: proc_open(/dev/null): failed to open stream: Operation not permitted2012BFR1153,
editor = {Symantec},
author = {Joji Hamada},
title = {Anaru malware now live and ready to steal},
date = {Error: Invalid time.},
month = Error: Invalid time.,
year = {2012},
howpublished = {\url{http://www.symantec.com/connect/ko/blogs/anaru-malware-now-live-and-ready-steal}},
}