The life cycle of web server botnet recruitment
Jump to navigation
Jump to search
(Publication) Google search: [1]
| The life cycle of web server botnet recruitment | |
|---|---|
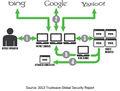
| |
| Botnet | |
| Malware | |
| Botnet/malware group | |
| Exploit kits | |
| Services | |
| Feature | |
| Distribution vector | |
| Target | |
| Origin | |
| Campaign | |
| Operation/Working group | |
| Vulnerability | |
| CCProtocol | |
| Date | 2013 / 2013-03-06 |
| Editor/Conference | Trustwave |
| Link | http://blog.spiderlabs.com/2013/03/the-life-cycle-of-web-server-botnet-recruitment.html blog.spiderlabs.com (blog.spiderlabs.com Archive copy) |
| Author | Ryan Barnett |
| Type | Blogpost |
Abstract
“ Over the course of the past year, my team has monitored and analyzed vast amounts of data within our Web honeypots and shared intelligence in our [Honeypot Alert] blog posts. In this blog post, we want to illustrate the most common methods botnet owners use to compromise websites and make them part of their army. The data in this section shows examples of code snippets and log file entries from real captured attacks.
Bibtex
@misc{Lua error: Cannot create process: proc_open(/dev/null): failed to open stream: Operation not permitted2013BFR1314,
editor = {Trustwave},
author = {Ryan Barnett},
title = {The life cycle of web server botnet recruitment},
date = {06},
month = Mar,
year = {2013},
howpublished = {\url{http://blog.spiderlabs.com/2013/03/the-life-cycle-of-web-server-botnet-recruitment.html blog.spiderlabs.com}},
}