Panel Supern0va et virus gendarmerie
(Publication) Google search: [1]
| Panel Supern0va et virus gendarmerie | |
|---|---|
| |
| Botnet | Supern0va |
| Malware | |
| Botnet/malware group | |
| Exploit kits | |
| Services | |
| Feature | |
| Distribution vector | |
| Target | |
| Origin | |
| Campaign | |
| Operation/Working group | |
| Vulnerability | |
| CCProtocol | |
| Date | 2012 / 2012/06/05 |
| Editor/Conference | Malekal Morte |
| Link | http://www.malekal.com/2012/06/05/panel-supern0va-et-virus-gendarmerie/ www.malekal.com (www.malekal.com Archive copy) |
| Author | Malekal Morte |
| Type | |
Abstract
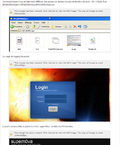
“ Un ransomware Virus gendarmerie différent des autres (ce dernier n’a pas de fonction de lock) : O4 – HKLM..Run: [M1qlOHhkvQqm] C:M1qlOHhkvQqmM1qlOHhkvQqm.exe
L’accès est possible, le panel se nome supern0va – la liste des PC infectés.
Bibtex
@misc{Lua error: Cannot create process: proc_open(/dev/null): failed to open stream: Operation not permitted2012BFR1088,
editor = {Malekal Morte},
author = {Malekal Morte},
title = {Panel Supern0va et virus gendarmerie},
date = {05},
month = Jun,
year = {2012},
howpublished = {\url{http://www.malekal.com/2012/06/05/panel-supern0va-et-virus-gendarmerie/ www.malekal.com}},
}