ZeuS
Jump to navigation
Jump to search
The printable version is no longer supported and may have rendering errors. Please update your browser bookmarks and please use the default browser print function instead.
(Botnet) Link to the old Wiki page : [1] / Google search: [2]
| ZeuS | |
|---|---|
| Alias | |
| Group | Banking |
| Parent | |
| Sibling | |
| Family | |
| Relations | Variants: Sibling of: |
| Target | Microsoft Windows |
| Origin | |
| Distribution vector | |
| UserAgent | |
| CCProtocol | HTTP (Centralized) |
| Activity | 2006 / |
| Status | |
| Language | |
| Programming language | |
| Operation/Working group | Operation b71 |
Introduction
ZeuS est un cheval de Troie qui dérobe des informations bancaires par enregistrement de frappe et récupération de formulaire.
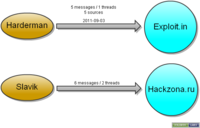
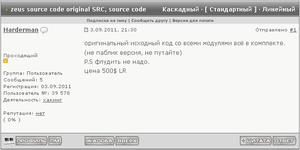
Début mai 2011, le code source de la version 2.0.8.9 a été rendu public. La publication de la source a permis de sortir des variantes du cheval de troie. La première variante observée a été IceIX vendu 1800$.
Descendance: IceIX, Citadel, Gameover, Murofet/Licat
Features
Associated images
Checksums / AV databases
Publications
File:ZeuS.PNG ZeuS v2.0.8.9 |
File:Builder ICE IX.jpg IceIX v1.0.5 |