Anonymous supporters tricked into installing ZeuS trojan
Jump to navigation
Jump to search
The printable version is no longer supported and may have rendering errors. Please update your browser bookmarks and please use the default browser print function instead.
(Publication) Google search: [1]
| Anonymous supporters tricked into installing ZeuS trojan | |
|---|---|
| |
| Botnet | ZeuS |
| Malware | Zbot |
| Botnet/malware group | |
| Exploit kits | |
| Services | |
| Feature | |
| Distribution vector | |
| Target | |
| Origin | |
| Campaign | |
| Operation/Working group | |
| Vulnerability | |
| CCProtocol | |
| Date | 2012 / |
| Editor/Conference | Symantec |
| Link | http://www.symantec.com/connect/ko/blogs/anonymous-supporters-tricked-installing-zeus-trojan (Archive copy) |
| Author | |
| Type | |
Abstract
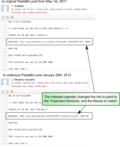
“ In 2011, dozens of Anonymous members who participated in distributed denial-of-service (DDoS) attacks in support of Anonymous hacktivism causes were arrested. In these DDoS attacks, supporters using the Low Orbit Ion Cannon denial-of-service (DoS) tool would voluntarily include their computer in a botnet for attacks in support of Anonymous. In the wake Anonymous member arrests this week, it is worth highlighting how Anonymous supporters have been deceived into installing ZeuS botnet clients purportedly for the purpose of DoS attacks. The ZeuS client does perform DoS attacks, but it doesn’t stop there. It also steals the users' online banking credentials, webmail credentials, and cookies.
Bibtex
@misc{Lua error: Cannot create process: proc_open(/dev/null): failed to open stream: Operation not permitted2012BFR907,
editor = {Symantec},
author = {},
title = {Anonymous supporters tricked into installing ZeuS trojan},
date = {23},
month = Apr,
year = {2012},
howpublished = {\url{http://www.symantec.com/connect/ko/blogs/anonymous-supporters-tricked-installing-zeus-trojan}},
}